In an age where cyberattacks, data breaches, and digital fraud are growing at an alarming rate, traditional security models often fall short. That’s where blockchain technology steps in—not just as the backbone of cryptocurrencies but as a powerful ally in cybersecurity and data protection.
In this blog, we’ll explore how blockchain is revolutionizing cybersecurity, why it’s considered virtually tamper-proof, and how it’s being used to secure digital ecosystems.
What Is Blockchain?
Blockchain technology is a decentralized digital ledger that records transactions across a network of computers in a way that ensures transparency, immutability, and security. Each transaction is grouped into a block, and these blocks are cryptographically linked to form a chain.
What makes blockchain special?
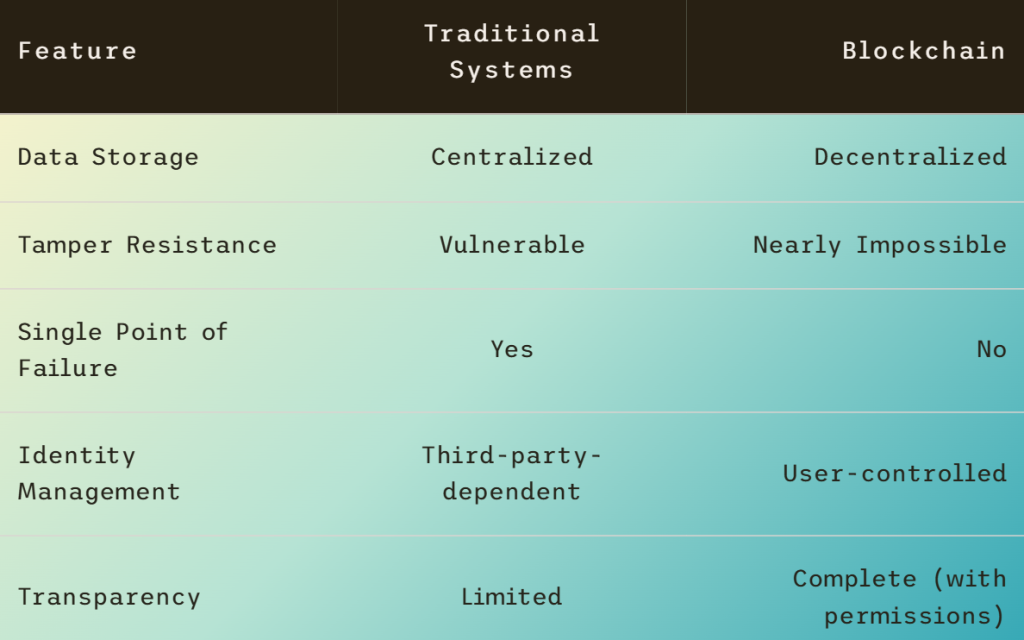
- It’s decentralized—no single point of failure
- It’s immutable—data once recorded cannot be altered
- It’s transparent—all changes are visible to all nodes
How Blockchain Enhances Cybersecurity
1. Decentralization Reduces Attack Surfaces
Most cyberattacks target centralized servers. Blockchain eliminates the need for a central server by distributing data across a peer-to-peer network. This structure makes it extremely difficult for hackers to corrupt or compromise the system.
2. Immutability Prevents Data Tampering
Once participants write data to the blockchain, no one can alter it without a consensus from the network. This tamper-resistant feature protects the integrity of critical information such as medical records, financial data, and legal documents.
3. Advanced Cryptography Strengthens Security
Blockchain secures data using cryptographic algorithms like SHA-256 and public-private key infrastructure (PKI). These methods protect information both in transit and at rest, reducing the risk of unauthorized access.
4. Improved Identity Management
Blockchain-based self-sovereign identity systems let users control their digital identities directly. By eliminating reliance on third parties, this approach reduces phishing, impersonation, and identity theft.
5. Smart Contracts Automate Security Protocols
Smart contracts are self-executing pieces of code stored on the blockchain. They automatically enforce predefined rules, such as access controls, ensuring that only authorized users can access or interact with sensitive data.
Real-World Applications of Blockchain in Cybersecurity
- Healthcare: Blockchain secures electronic health records (EHRs), providing tamper-proof histories while allowing controlled access among hospitals, doctors, and patients.
- Financial Services: Banks use blockchain to combat money laundering, protect digital wallets, and secure online transactions.
- IoT Security: The Internet of Things (IoT) often lacks robust security. Blockchain can secure device communications and authenticate users without centralized servers.
- Secure Voting Systems: Countries are experimenting with blockchain-based voting systems to prevent tampering, ensure transparency, and maintain voter anonymity.
- Supply Chain Integrity: Blockchain ensures product authenticity by providing end-to-end visibility into the supply chain, reducing counterfeiting and fraud.
Blockchain vs Traditional Cybersecurity
Limitations to Consider
While blockchain technology holds immense potential, it’s not a silver bullet. Consider these challenges:
- Scalability issues with some blockchain networks
- High energy consumption (especially Proof-of-Work blockchains)
- Regulatory uncertainty in many countries
- Lack of standardization across industries
These hurdles must be addressed before blockchain can become a mainstream cybersecurity tool.
Final Thoughts
As cyber threats grow more sophisticated, traditional defense mechanisms are struggling to keep pace. Blockchain offers a paradigm shift—promising a secure, decentralized, and transparent approach to protecting digital assets. Whether it’s securing financial systems or creating tamper-proof medical records, blockchain is emerging as a cornerstone of modern cybersecurity.
Investing in blockchain-based security is not just futuristic—it’s essential for building a resilient digital world.